
MindStudio AI Portfolio
Personal Portfolio of AI Agent Projects

Personal Portfolio of AI Agent Projects
Decryption of an XOR cipher

BadSuccessor attack for privilege escalation in Active Directory
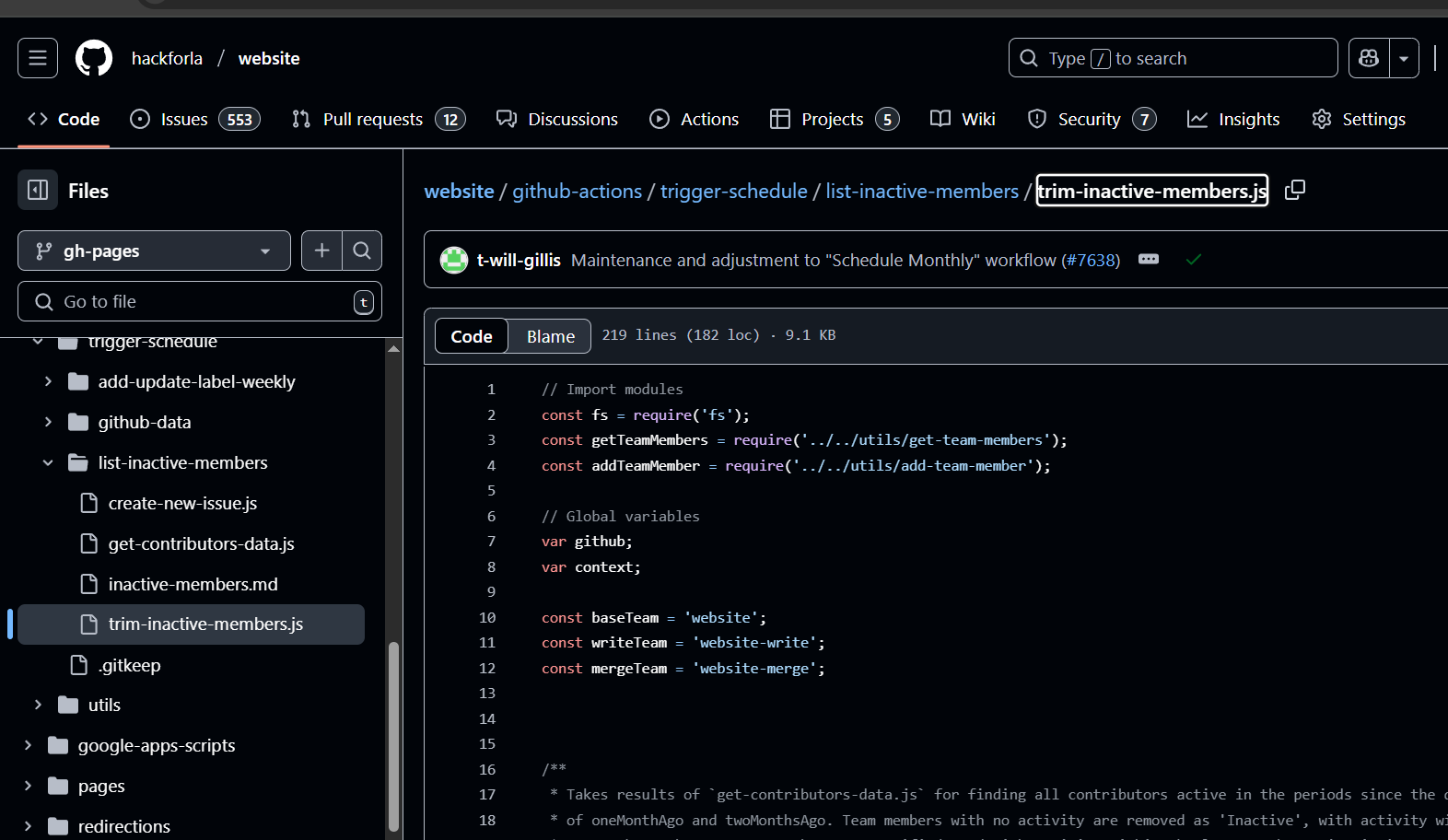
GitHub Actions Workflow for Identity and Access Management
CySky Notes Log Analysis

CySky Notes Forensics

CySky Notes Enumeration & Exploitation


Forensic investigation of disk image and network traces
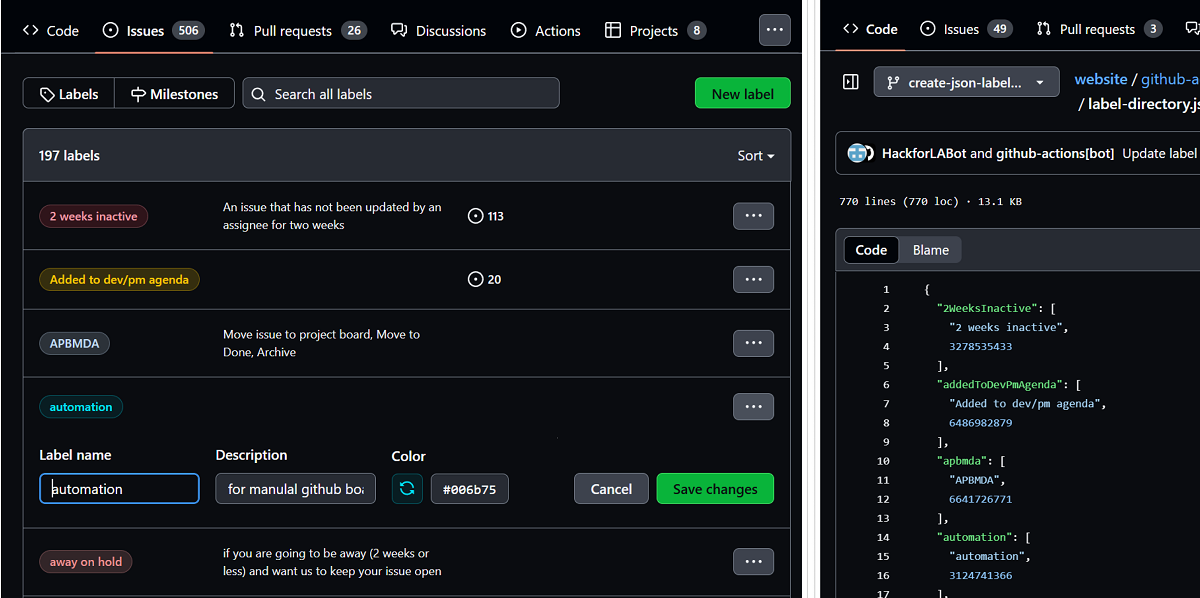
GitHub Actions Automation to Monitor Labels in Repo